Security > Security Monitoring > Overview
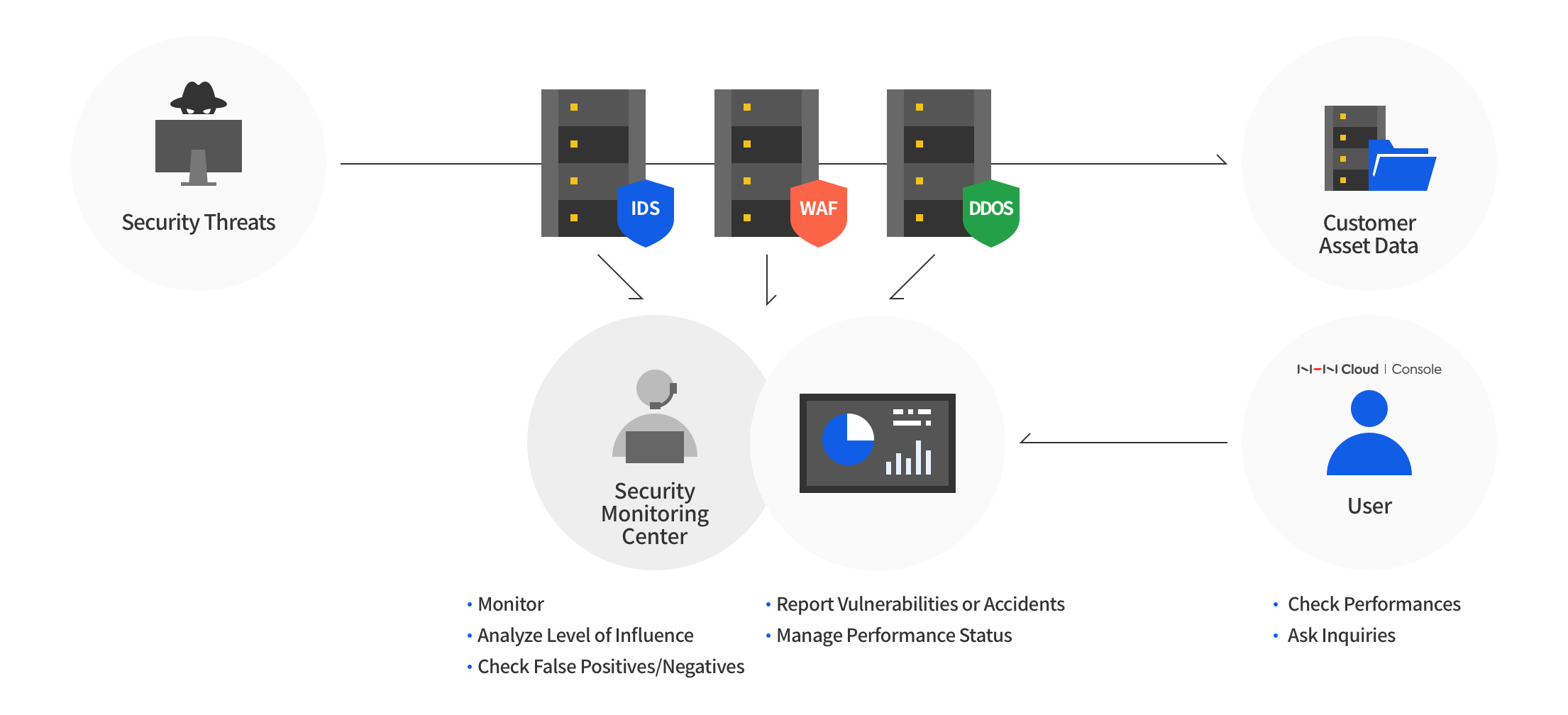
Security Monitoring, based on accumulated and verified IDS/SIEM patterns and risk management response system of NHN Cloud, provides 24/7 high-level security surveillance service by professional engineers.
Benefits
Security Monitoring by Controlled Security Center
- Equipped with full physical security control system (e.g. CCTV installed in all business areas, access control by fingerprint recognition, or magic mirror operations).
- Network divided for each work environment, control of information leakage and fortified pc security.
- Various dashboard screen configuration supported by audio and video equipment system, so as to detect and respond to real-time change of attacks.
- Service continuity ensured, and measures for interruptible power supply.
24/7 Cost-Efficient Professional Monitoring and Operation Services
- Seasoned security personnel with sufficient experience in a variety of hacking threats promptly determine if it is an incident and its influences.
- Detection patterns are applied with the latest trends of attacks, in order to prevent or fast respond to threats.
- Security monitoring services and cost-saving jobs, required for organizing and maintaining security works, are assigned to professionals so that IT personnel can focus on their main jobs.
- Helps to resolve difficulties in securing security staff from within.
Distinctive Next-Generation Remote Security Service
- Proves to be excellent in detection of attacks through powerful IDS/SIEM detection patterns which are verified throughout years of operation in NHN Cloud.
- Provides distinctive security monitoring service, by the combination of scenario-based SIEM detection pattern, not by simple pattern matching.
- Executes influence-verifying test in consideration of raw data and services for all threat attempts.
- Notifies for vulnerabilities and suspicious acts, by influence verification and in-depth analysis in packet dumps, which are more than simple event notifications.
Real-Time Security Monitoring Checks on Console
- Security monitoring detection and analysis can be immediately found on a console.
- Incidents are immediately recognized via network transmission, even during off-business hours.
- An event screen for IDS occurrence is provided via instance applied for security monitoring.
- Security monitoring work progress can be notified by email.
Main Features
Detection
- Support 24/7 security monitoring and sophisticated detection pattern of IDS/SIEM relevancy
Analysis
- Perform in-depth analysis by using raw event data and packet dumps.
- Apply our own security monitoring methodology to detect and classify threats right from wrong, and perform influence testing.
Response
- Provide and transmit information on identified weaknesses.
- Provide information on the route and weakness of intrusion in transmission and network.
- Perform follow-up responsive measures, like packet dumps, when an intrusion occurs, and support analysis.
Prevention
- Collect external data on a regular basis to create detection patterns for potential threats.
- Optimize patterns for error factors in real-time response to events, such as excessively false detection.
Data Supply
- Share work status via console at the support of the security monitoring WORK-FLOW system.
- Provide IDS event occurrence on dashboard.
- Deliver security monitoring status by email.
- Communicate on the phone when security incidents occur.
Reference
- WAF is available with the WEB Firewall service.
- DDoS attack can be prevented by DDoS Guard service.
Table of Contents
- Security > Security Monitoring > Overview
- Benefits
- Security Monitoring by Controlled Security Center
- 24/7 Cost-Efficient Professional Monitoring and Operation Services
- Distinctive Next-Generation Remote Security Service
- Real-Time Security Monitoring Checks on Console
- Main Features
- Detection
- Analysis
- Response
- Prevention
- Data Supply
- Reference